Coherence Diversity & Correlation Diversity
Wireless communication techniques are increasingly dependent on the knowledge of link qualities (channel state information) being acquired and properly exchanged among the network nodes. This task is closely dependent on how rapidly the corresponding channel gains vary (coherence intervals). Multiuser scenarios (nowadays called NOMA) often assume that different links experience the same fading speed, but in practice link coherence intervals may easily be different due to variations in node speeds or differences in scattering environment.
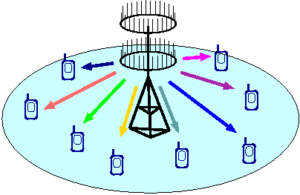
Our research has shown that the difference between link coherence intervals (fading speeds) gives rise to a new class of gains called coherence diversity. Our work has characterized the nature and extent of coherence diversity under a number of scenarios. These gains have been carefully analyzed in the broadcast (downlink), multiple access (uplink), as well as in the relay channel. Some of this work is on-going, especially when the channel state at the transmitter with respect to different users is unequal (perfect, stale, or non-existant). This concept has been investigated in both time and frequency.
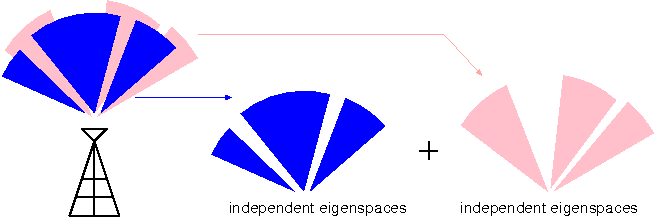
A related concept also exist in terms of spatial correlation between antennas. Especially in massive MIMO, antenna gains are not uncorrelated and, furthermore, the correlation of link gains varies between users. These differences can also give rise to gains, which are called antenna correlation diversity.
Wireless Hardware Trojans
Hardware Trojans are malicious circuits that are implemented in an Integrated Circuit (IC) by an adversary to interfere with its legitimate operations and/or steal sensitive information from it. Wireless networks are an attractive target for hardware Trojan attacks, since they exchange information over public channels. Together with Prof. Yiorgos Makris at UTD, the Nosratinia Lab has been a pioneer in the analysis of wireless Trojan threats and producing mitigation and detection strategies. Our work is based on the notion that wireless Trojans often operate a gap between the operational point of a circuit and its theoretical limit, which creates an opening for a malicious modification to exfiltrate information inconspicuously.
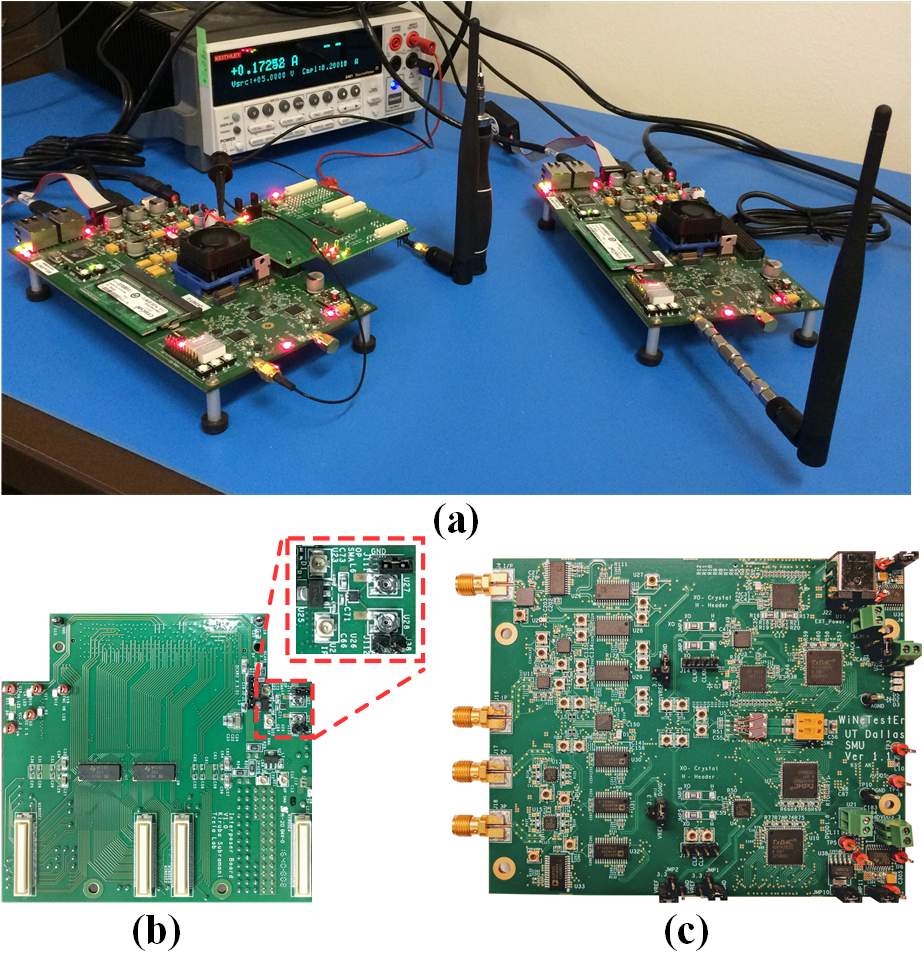
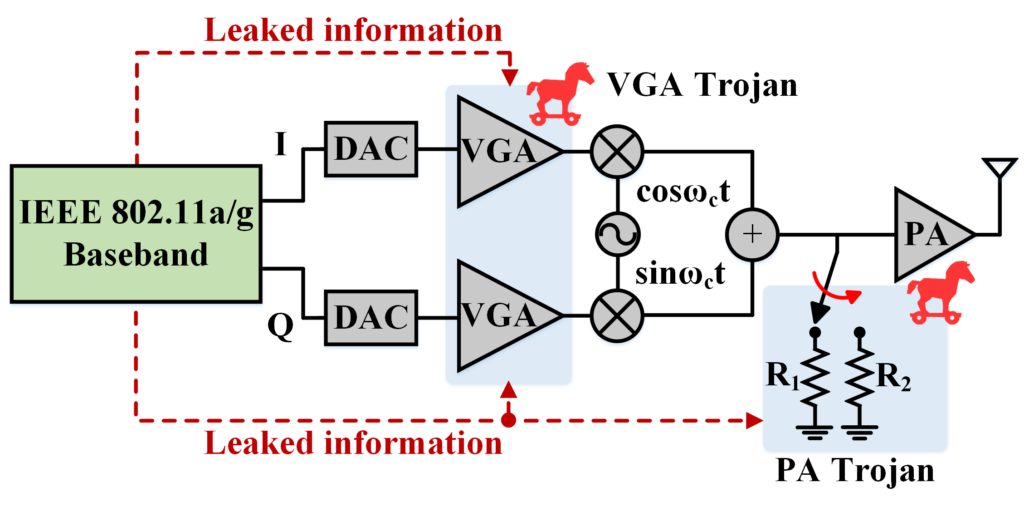
This principle has been demonstrated in impulse radio, as well as in the context of WiFi. These threats have been implemented at the circuit level and chip level, and their mitigation strategies demonstrated. Please see our publications for further detail.
Advanced Coding & Modulation
The first component of our research in this area is in collaboration with the University of Hawaii, and decomposes the communication stream into “microstreams” to fit the transmissions into the contours of available opportunities, in a manner that improves rates while limiting the damage of interference. As part of this activity, new results are obtained about the performance of discrete modulations in the interference channel.
The second component of this research is informed by recent developments in information theory indicating that a multi-level approximation to the physical channel has a capacity that is within a small SNR-independent gap to the capacity of the physical channel. Supported by preliminary results, this research operates on the hypothesis that a similar multi-level decomposition is a sound and fruitful approach for the design of high-performance coded modulations for multi-terminal networks.
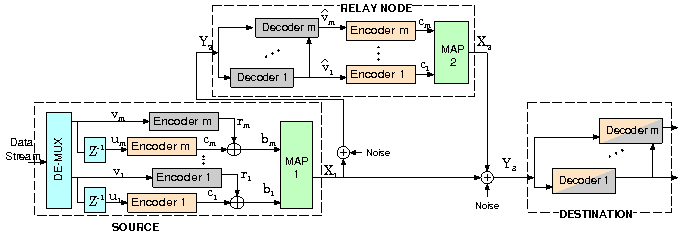
Research tasks investigate the proposed methodology to produce efficient coded modulation architectures for a variety of multi-terminal networks. This hypothesis has been confirmed in the postive in the context of the broadcast channel and the relay channel, where efficient coding and modulation techniques have been found that utilize easily available and computationally efficient binary error control codes but also are able to operate very close to the theoretical capacity of the channel.
You must be logged in to post a comment.