Cooperation for Resolvability and Security
Secure communication is often characterized as information exchange between two legitimate parties (Alice and Bob) whose content must be kept secret from an adversary (Eve). The modern approach to secrecy coding is through resolvability, i.e., the idea of inducing a known distribution at the output of Eve. Motivated and fueled by extensive past work in the Nosratinia Lab on cooperative communication, we investigate (together with Prof. Matthieu Bloch of Georgia Tech) various cooperation strategies between two or more legitimate parties and their impact on channel resolvability and security/secrecy against an adversary.
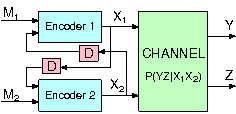
This investigation has produced interesting and unexpected results. In particular, new cooperative mechanisms were discovered in the multiple access channel, where the cooperation itself occurs through a virtual embedded wiretap channel that alows two users to exchange randomness without the knowledge of Eve. These new cooperative secrecy mechanisms go beyond earlier discoveries which were mostly based on cooperative jamming. Please see our publications for further detail.
Covert Communication
Covert communication is the act of communicating with a legitimate party (Alice to Bob) while an adversary (Warden) must not be able to even tell that communication is taking place at all. This is a very restrictive and difficult condition, similar in form to steganography (watermarking). It has been known that for many channels, only $O(\sqrt{n})$ bits can be transmitted per $n$ transmissions, thus the rate is zero. Our research explores this interesting problem, and seeks instances where nonzero rate is possible under realistic conditions.
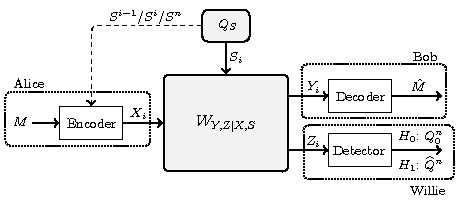
Recently, it was shown that if the channel has states and if the state is known at the transmitter, then non-zero covert rates are possible but may require a secret key. Our results show that it is possible to do away with the external key requirement, thus bringing covert communication one step closer to practicality.
Wireless Hardware Trojans
Hardware Trojans are malicious circuits that are implemented in an Integrated Circuit (IC) by an adversary to interfere with its legitimate operations and/or steal sensitive information from it. Wireless networks are an attractive target for hardware Trojan attacks, since they exchange information over public channels. Together with Prof. Yiorgos Makris at UTD, the Nosratinia Lab has been a pioneer in the analysis of wireless Trojan threats and producing mitigation and detection strategies. Our work is based on the notion that wireless Trojans often operate a gap between the operational point of a circuit and its theoretical limit, which creates an opening for a malicious modification to exfiltrate information inconspicuously.
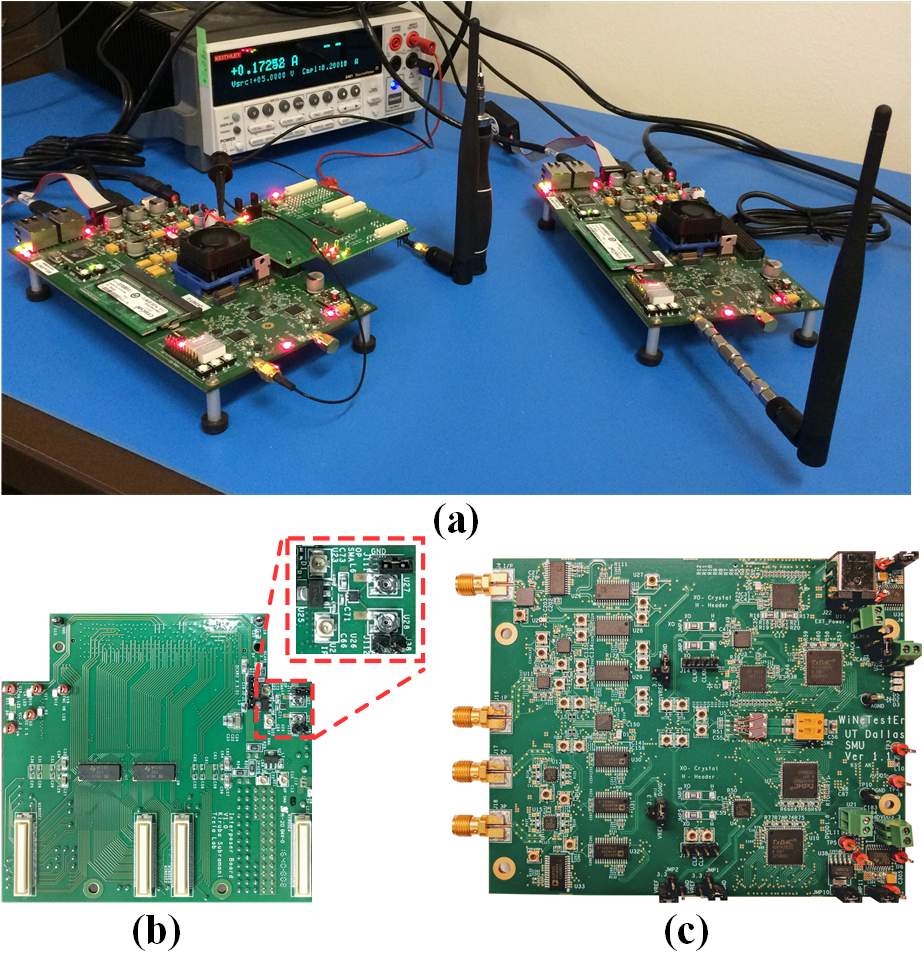
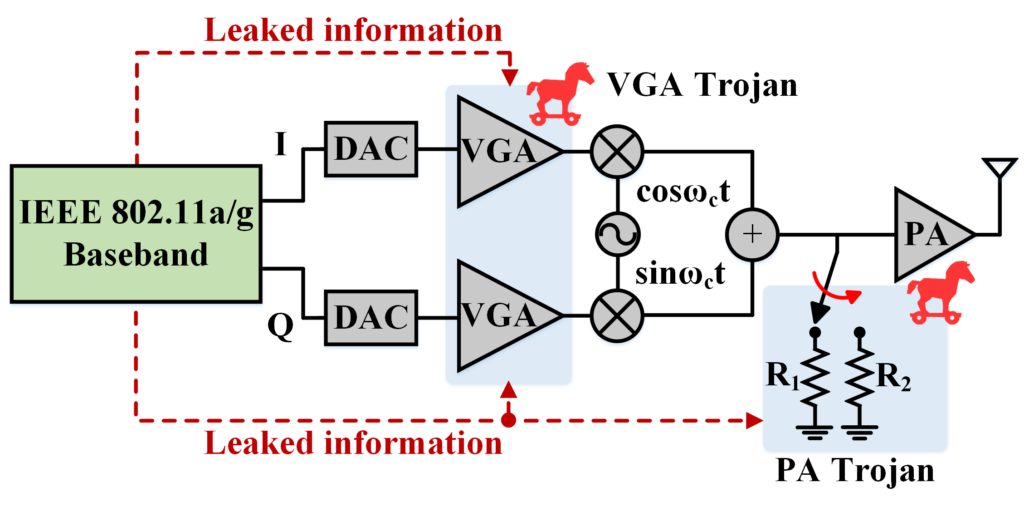
This principle has been demonstrated in impulse radio, as well as in the context of WiFi. These threats have been implemented at the circuit level and chip level, and their mitigation strategies demonstrated. Please see our publications for further detail.
You must be logged in to post a comment.